How the UID2 Token Is Created
This article describes how the UID2 token that the publisher sends in the bidstream is created. The process is the same for advertisers creating UID2 tokens for conversion pixels. It does not apply to tokenized sharing, where raw UID2s are encrypted into UID2 tokens before sending to another sharing participant.
When a publisher sends a user's DII—hashed or unhashed email addresses or phone numbers—to the UID2 Operator, and in return receives a UID2 token to use for targeted advertising, there is a very specific sequence of processing steps that occurs along the way.
Some preliminary steps are taken by the publisher, but most of the processing steps are done by the UID2 Operator.
It's very important that the publisher steps are performed in the correct sequence:
- When steps are performed in sequence, the resulting value can be recognized as related to other UID2 identifier types generated from online activity by the same individual: the underlying raw UID2 matches the raw UID2s generated by other UID2 participants from the same DII, and therefore the token is suitable for targeted advertising.
- If steps are taken out of sequence, the resulting value cannot be related to other UID2 identifiers generated from online activity by the same individual, and therefore the token is not suitable for targeted advertising.
For a summary, see Steps to Create a UID2 Token. For an example in diagram form, see Creating a UID2 Token—Example.
Steps to Create a UID2 Token
The following table shows the steps for creating a UID2 token from DII, the sequence, and who performs each step.
For an example with sample values, see Creating a UID2 Token—Example.
| Step | Action | Who Does It? | Documentation |
|---|---|---|---|
| 1 | Normalize. | Email: Publisher or UID2 Operator Phone number: Publisher must normalize | Email Address Normalization Phone Number Normalization |
| 2 | Apply SHA-256 hashing to the normalized email address. | Publisher or UID2 Operator | Email Address Hash Encoding Phone Number Hash Encoding |
| 3 | Apply Base64 encoding to the SHA-256 hash. | Publisher or UID2 Operator | Email Address Hash Encoding Phone Number Hash Encoding |
| 4 | Send value to UID2 Operator via the POST /token/generate endpoint, an SDK, Prebid.js, or another supported integration. | Publisher | Various: for a summary, see Implementation Resources |
| 5 | Perform multiple steps including hashing and adding the secret salt value to create a raw UID2. | UID2 Operator | Not applicable: these steps are all performed by the UID2 Operator. |
| 6 | Encrypt the raw UID2 to create a UID2 token. | UID2 Operator | Not applicable: performed by the UID2 Operator. |
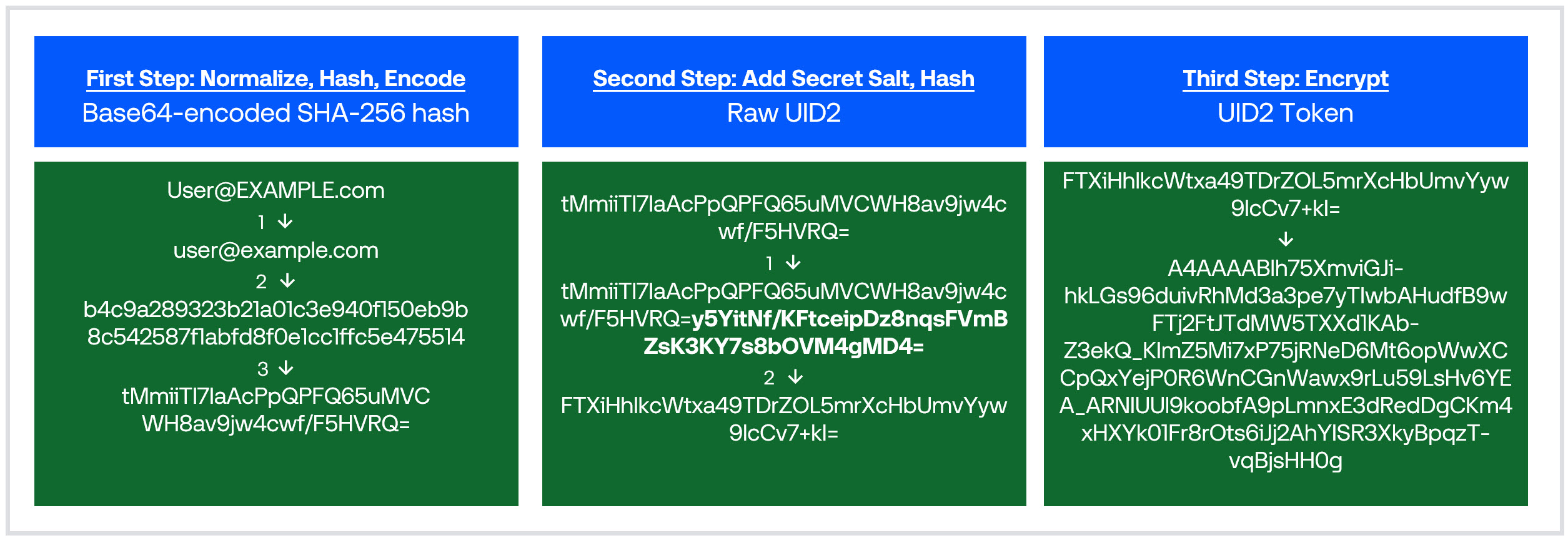
Creating a UID2 Token—Example
The following diagram shows the high-level steps for creating a raw UID2 (first column, second column) and then a UID2 token (third column).
The publisher can send a request to the POST /token/generate endpoint or use one of the other integration options, such as an SDK or Prebid. Whatever the integration option, the result is a UID2 token—an encrypted value that the publisher can send in the bidstream for targeted advertising.